Install Solaris 11.2
1. Boot DVD Image Solaris 11.2
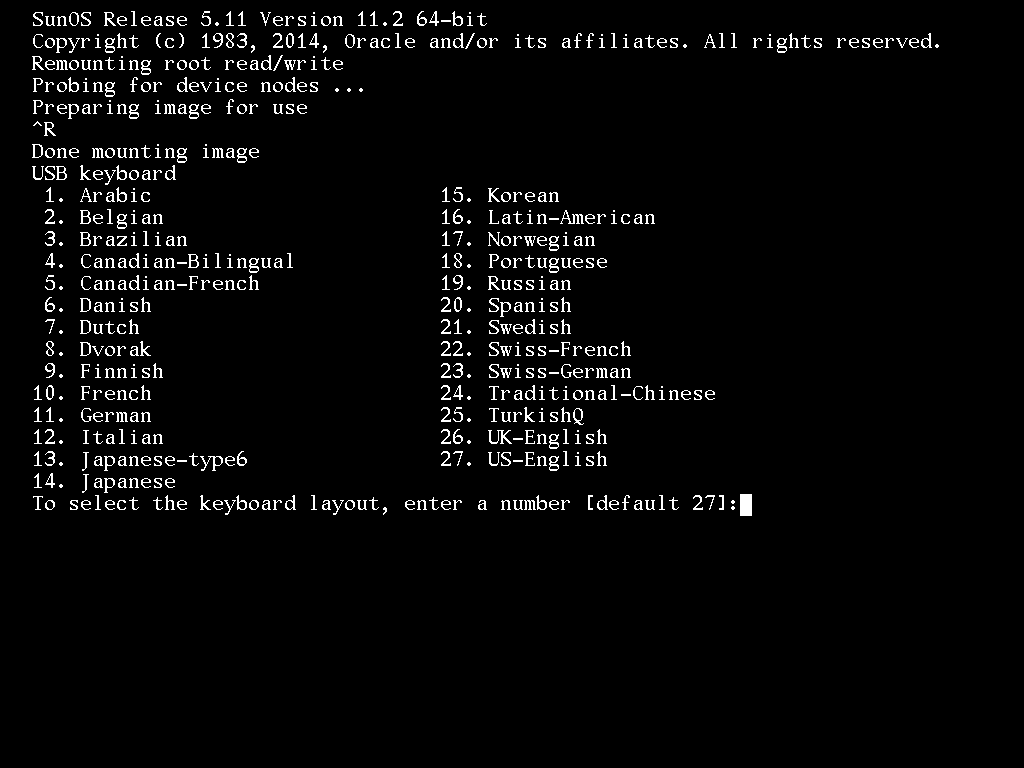
2. Select the keyboard layout [27 = US-English]
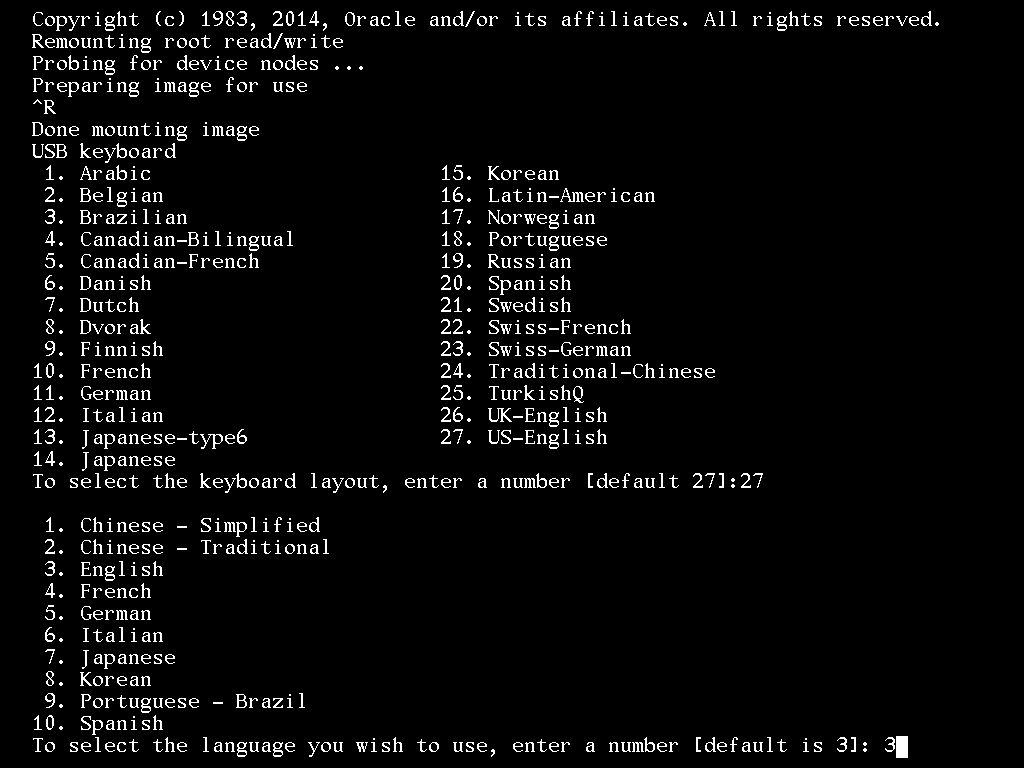
3. Select the language [3 = English]
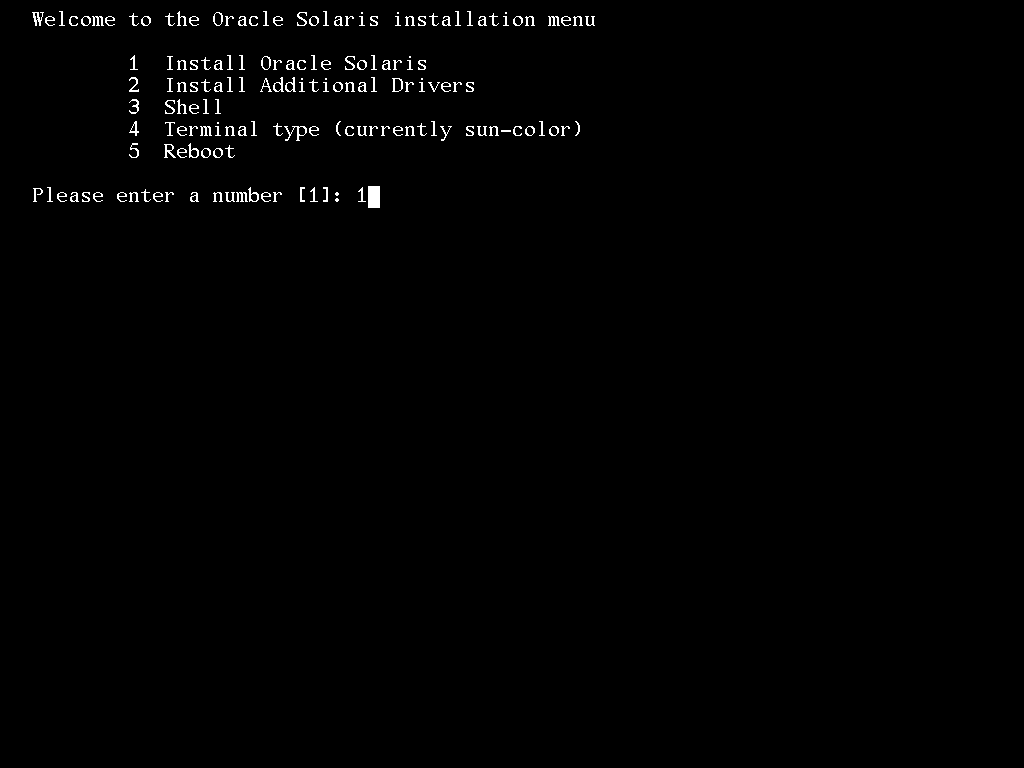
4. Please enter a number 1 [Install Oracle Solaris]
5. Select the “F2”
6. Select the “Local Disks” and “F2”
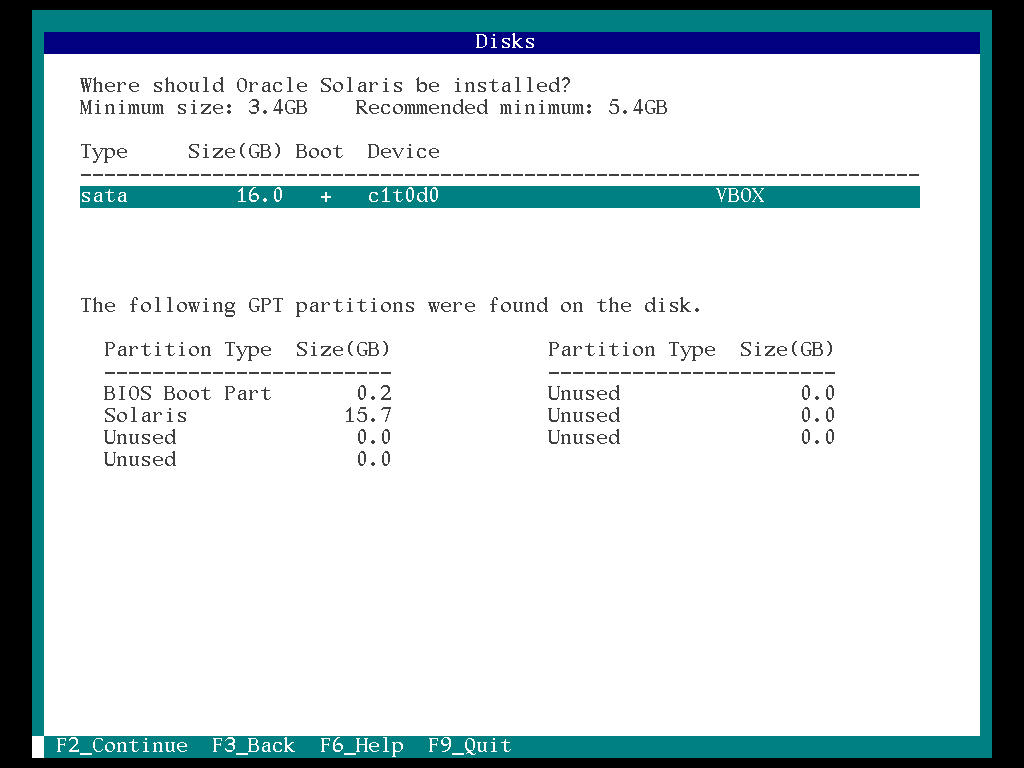
7. Select the “Disk (sata = c1t0d0)” and “F2”
8. Select the “Use the entire disk” and “F2”
9. Enter a name for this server and select “F2”
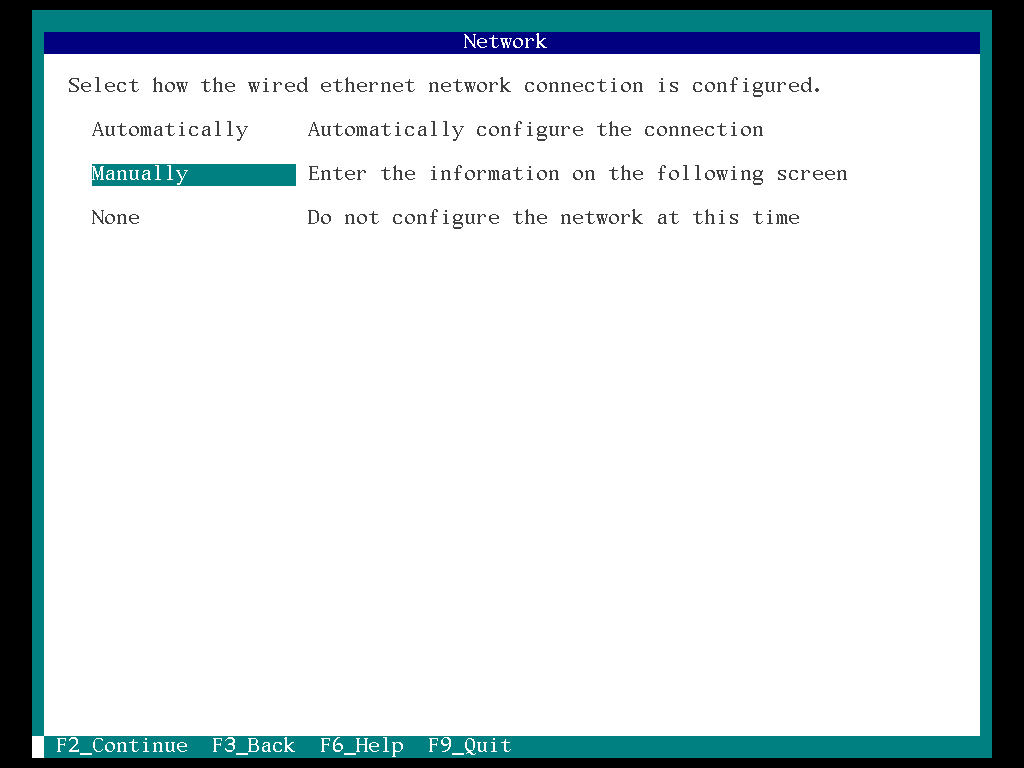
10. Select the “Manually” and “F2”
11. Enter the configuration for this network connection and select “F2”
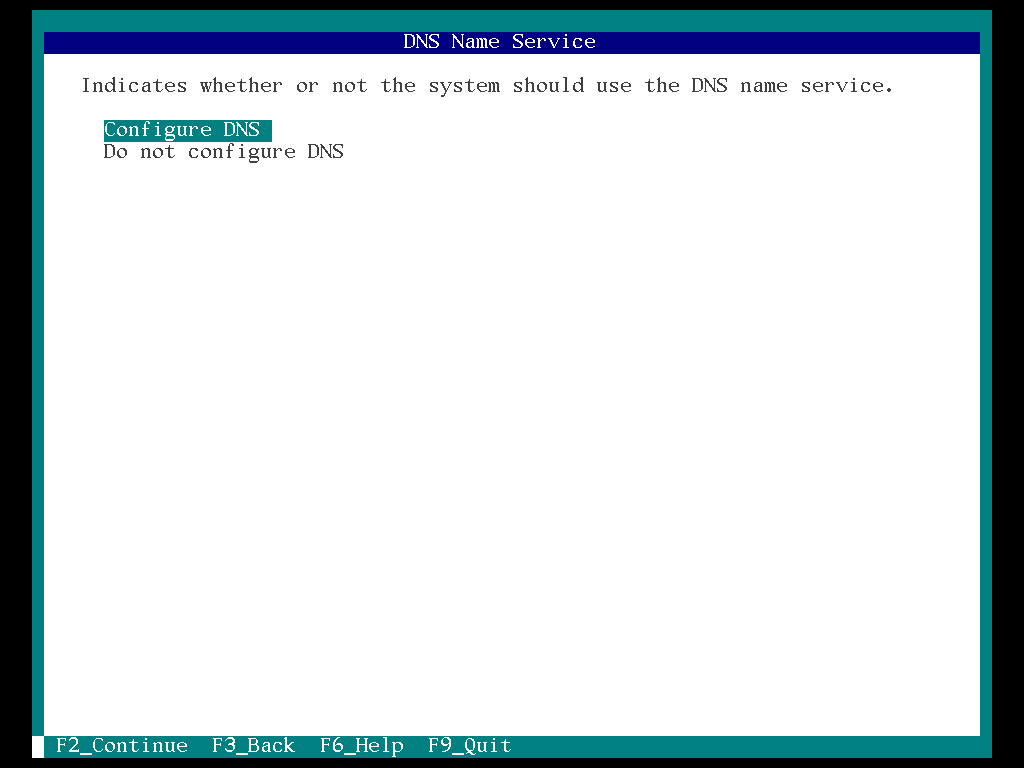
12. Select the “Configure DNS” and “F2”
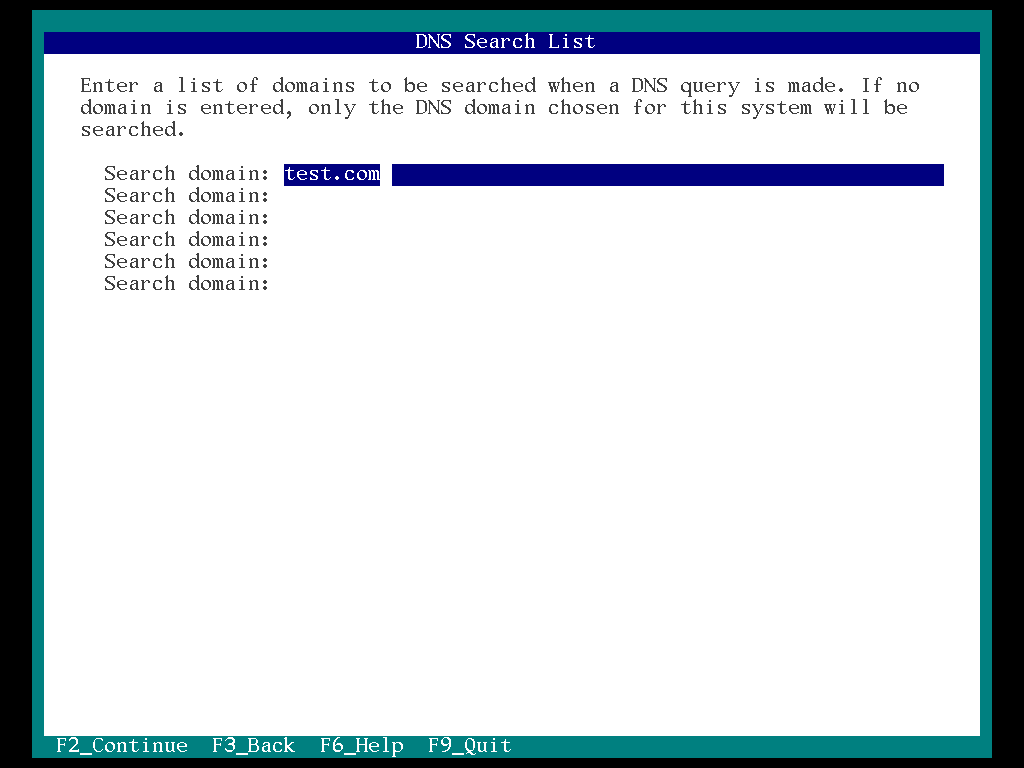
13. Enter a list of domains and select “F2”
14. Enter the IP address of DNS server and select “F2”
15. Select the “None” and “F2”
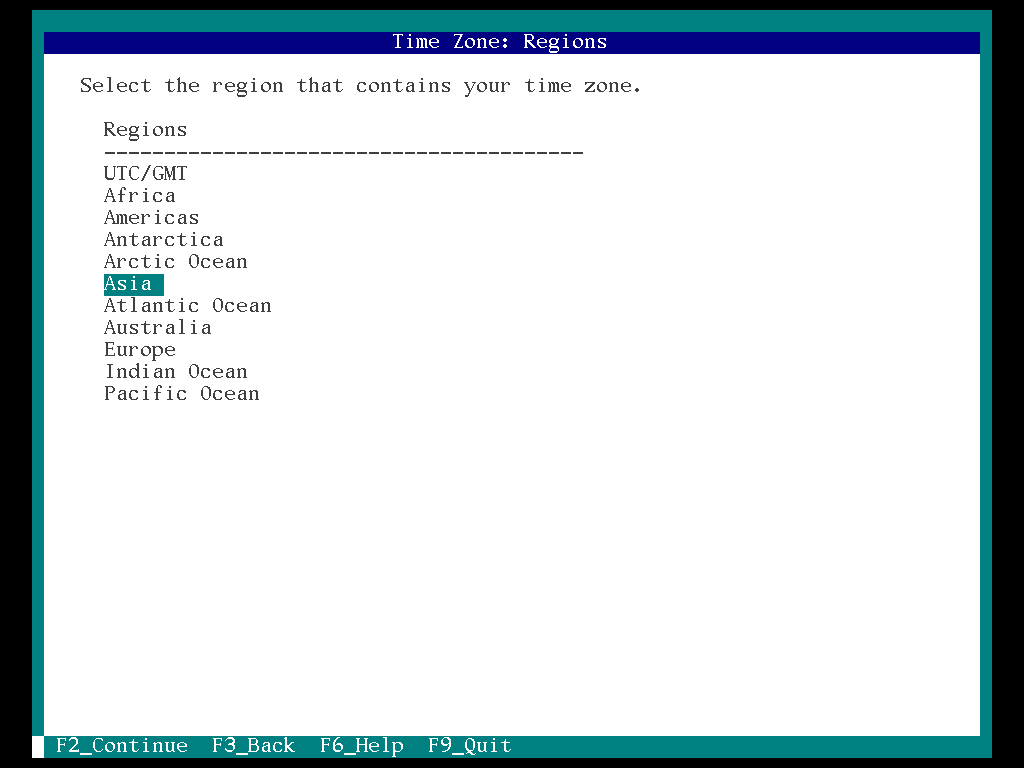
16. Select the “Region (Asia)” and “F2”
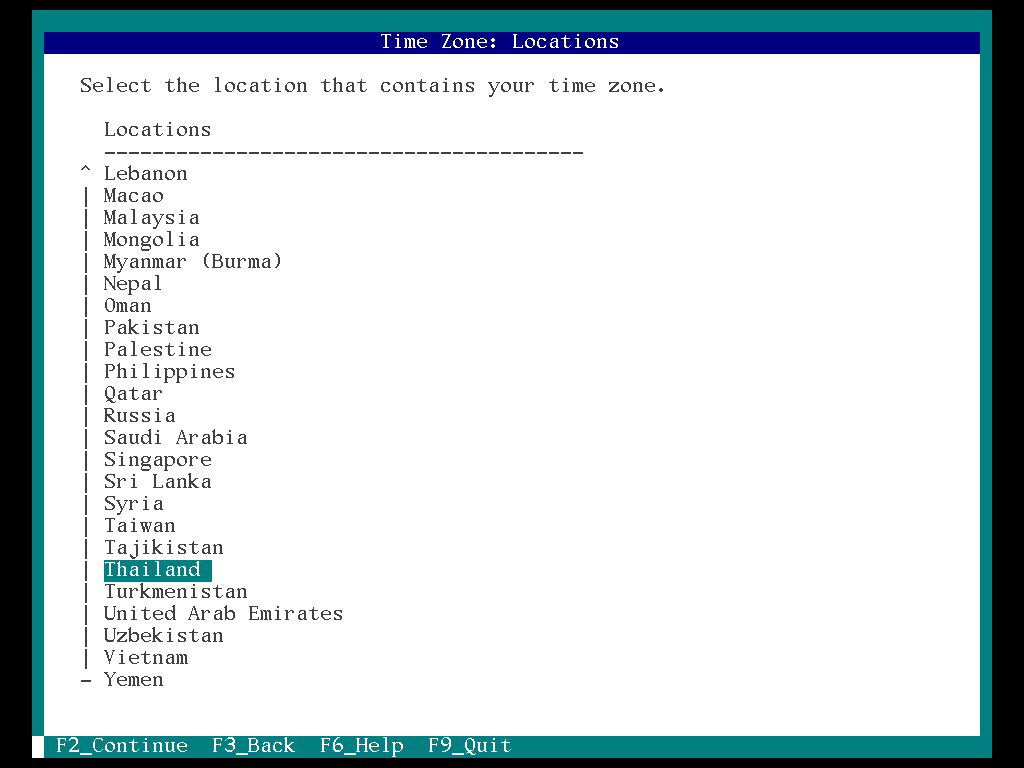
17. Select the “Location (Thailand)” and “F2”
18. Select the “Time Zones (Asia/Bangkok)” and “F2”
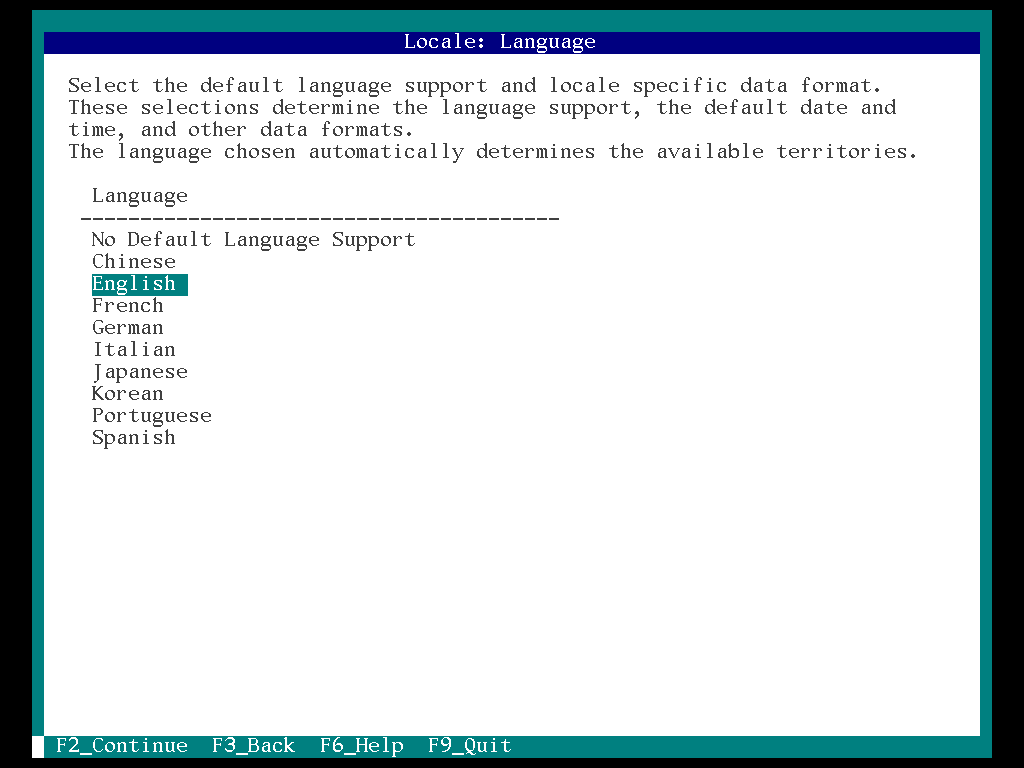
19. Select the “Language support (English)” and “F2”
20. Edit the date ant time and select “F2”
21. Select your keyboard “US-English” and “F2”
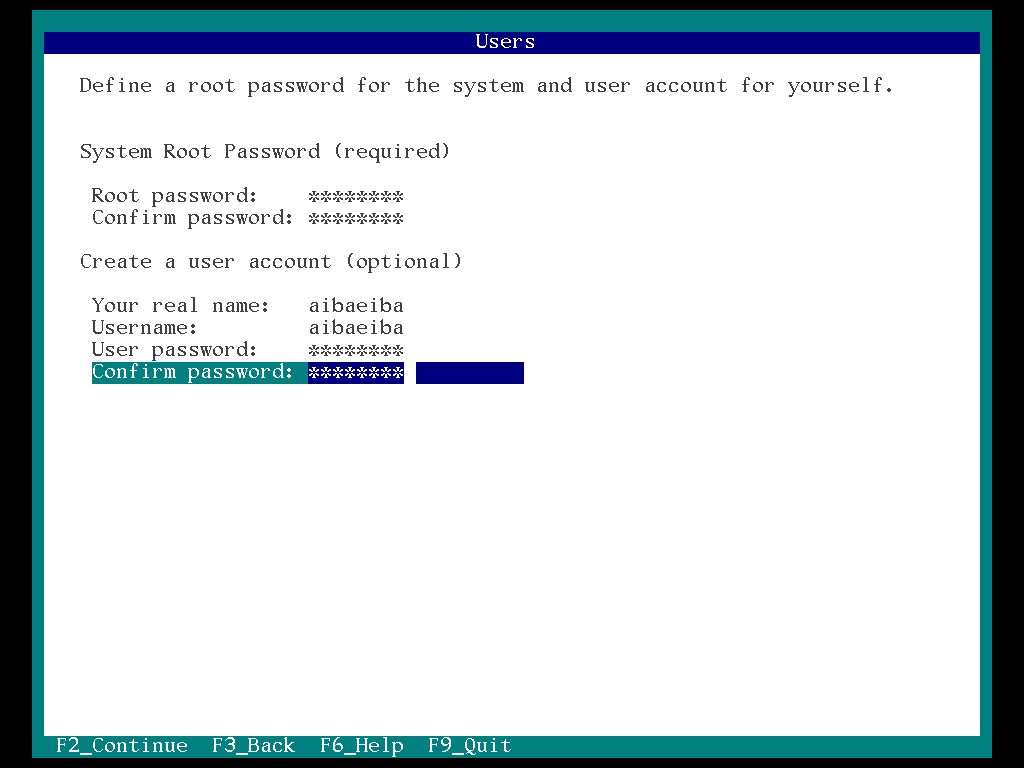
22. Enter the root password , create user account and select “F2”
23. Select the language “United States” and “F2”
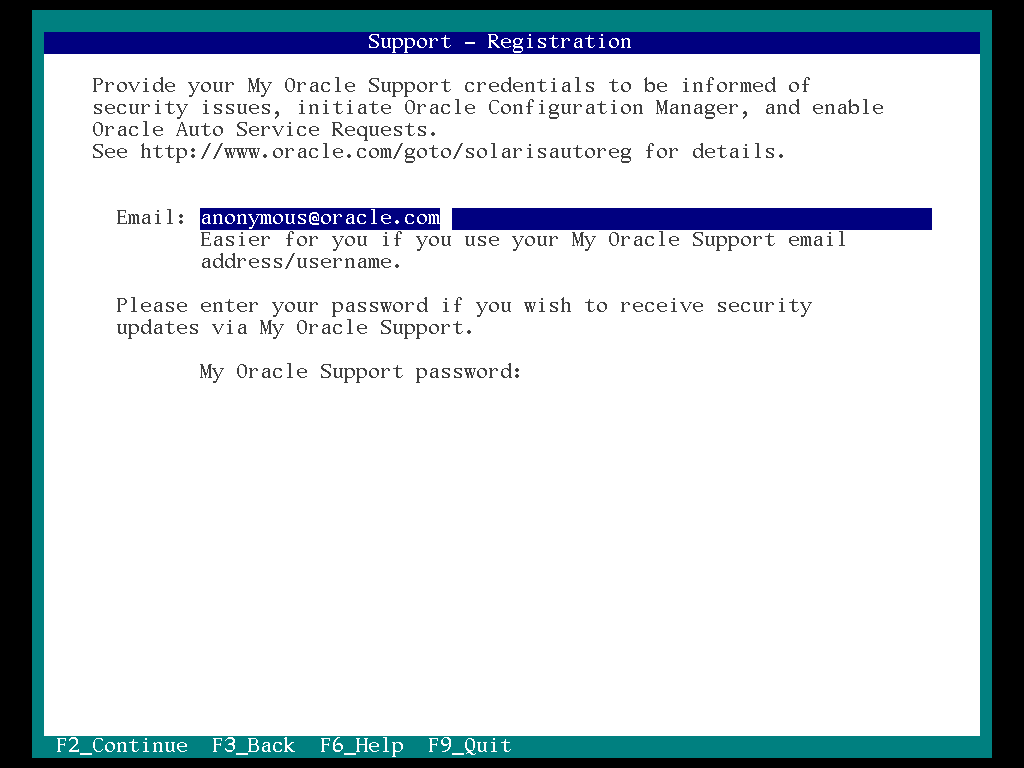
24. Select the “F2”
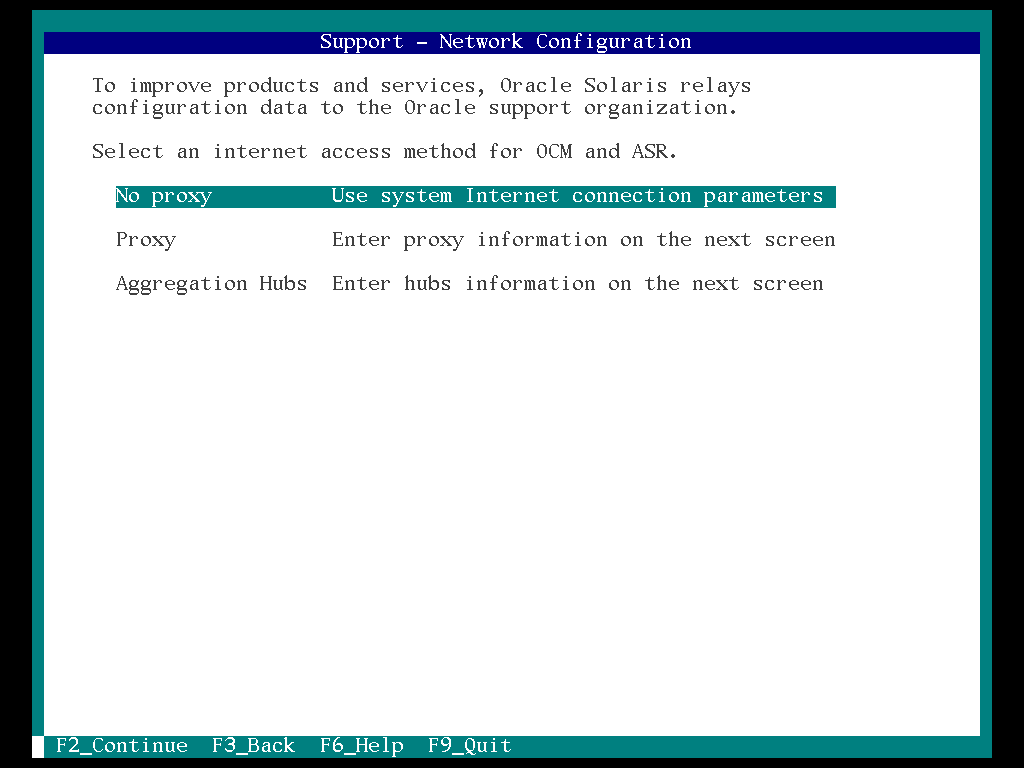
25. Select the proxy server “No proxy” and “F2”
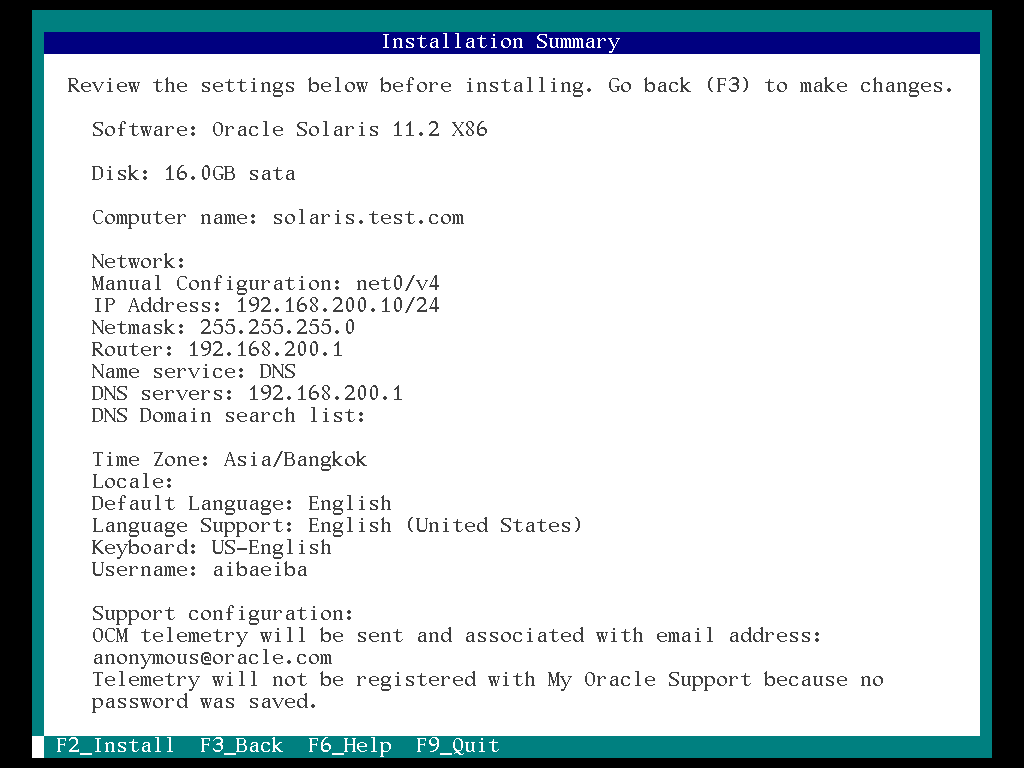
26. Review the settings summary and select the “F2”
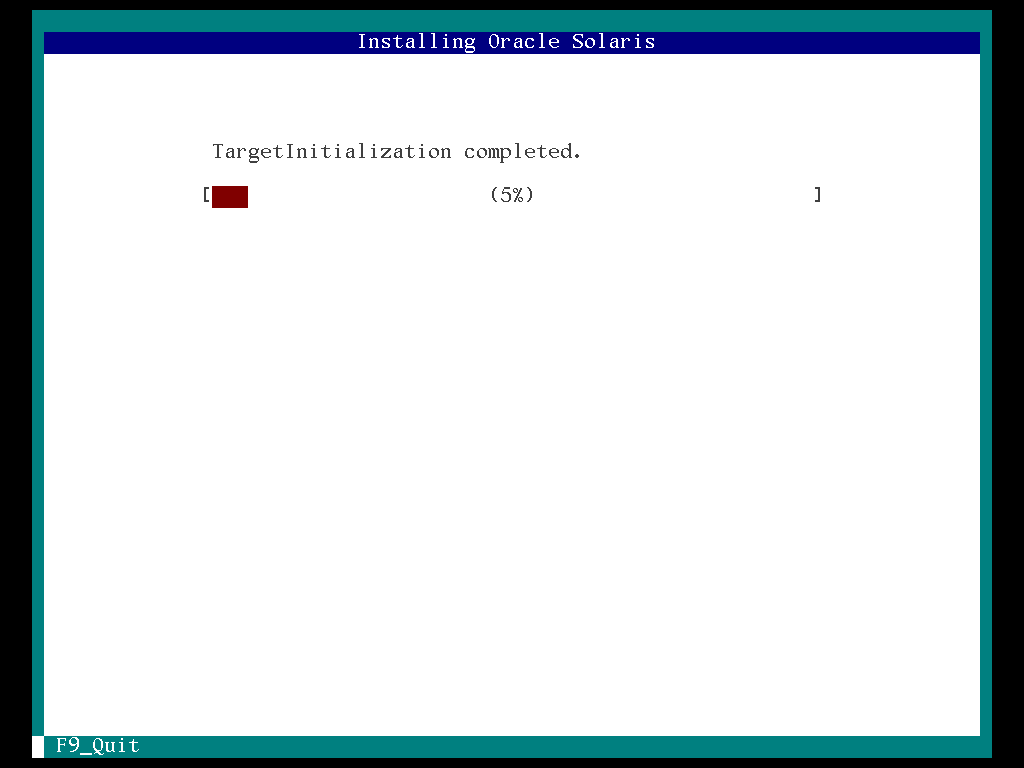
27. Installing Oracle Solaris
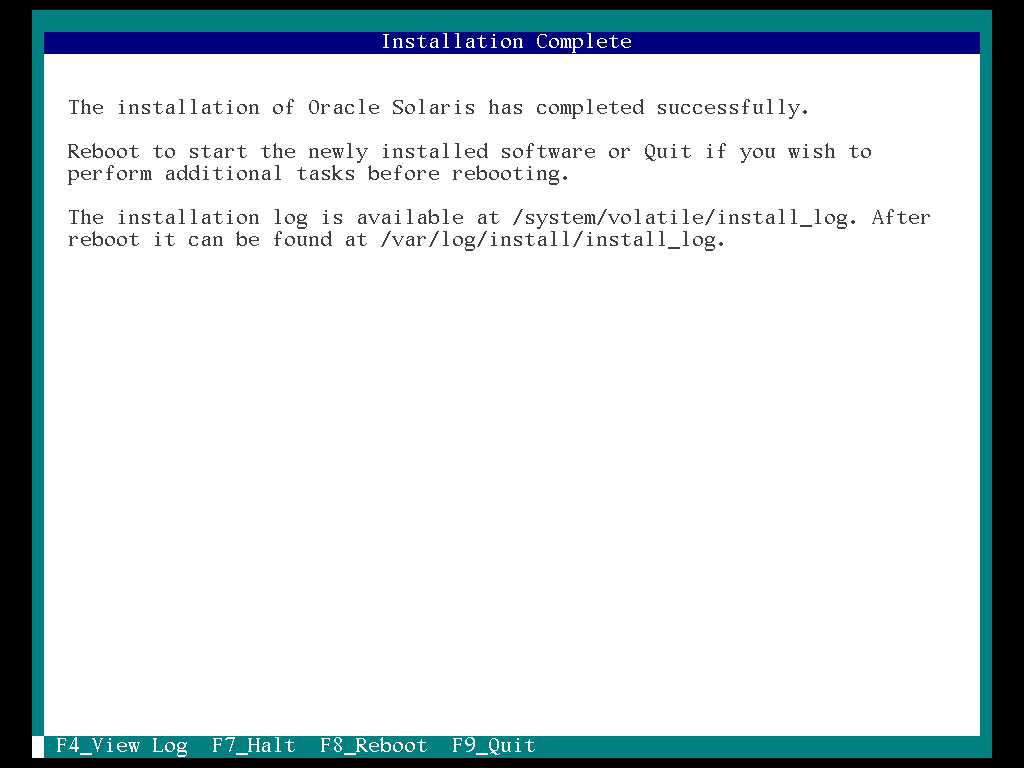
28. Installation complete and select the “F8”
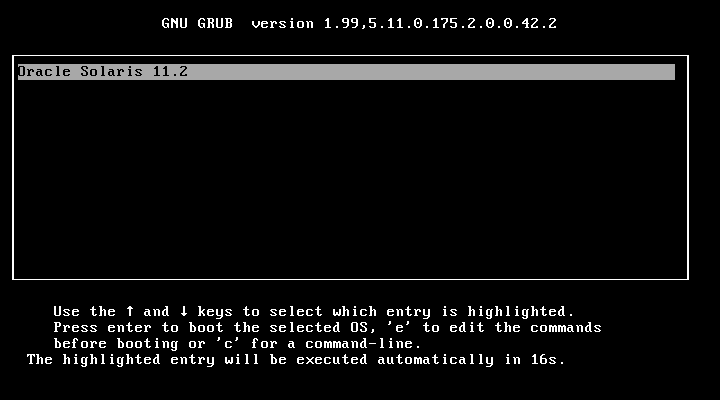
29. Select the “Oracle Solaris 11.2”
30. Loading SunOS (Solaris 11)
31. Please login OK!